字體:小 中 大
字體:小 中 大 |
|
|
|
| 2019/10/28 00:09:49瀏覽145|回應0|推薦0 | |
這篇是這幾年來。懷疑中國政府是否有「國家的駭客網軍」,被傳說專門監視各國公家機關及國際上大企業的網路傳遞,按照IP位址,位在上海浦東新區的高橋鎮作發信,代號是「61398」,是和中國軍隊有買賣生意往來的邁瑞醫療器材公司(Mindray),僅知道在中國境內有駭客,但不知道是否為官方單位或說是受其要求,後來雖然不了了之,但是成為華為技術和中興通訊等廠商被美國政府封殺的開端。
Cybercrime Smoking gun Evidence is mounting that China’s government is sponsoring the cybertheft of Western corporate secrets. What should America do to stop it? Feb 23rd 2013 | SHANGHAI |From the print edition · ·
FOR years, intelligence agencies and private security experts have warned that Chinese hackers are trying to steal Western corporate secrets. The cries have grown ever louder as the attacks have become bolder and signs of government involvement have surfaced. In a forthcoming book, Eric Schmidt, the executive chairman of Google, reportedly brands China “the most sophisticated and prolific” hacker of foreign companies. Chinese hacking has outraged many American politicians, leading to noisy hearings in Congress and a backlash against Chinese firms. Earlier this month the Obama administration declared its intention to go on the cyber-security offensive. Europe, China’s biggest trade partner, is angry, too. The European Commission is considering forcing hacked companies to reveal their woes to the authorities. In this section · Smoking gun Related topics · Hacking · Peoples Liberation Army (China) · China The Chinese government has always hotly denied the accusations. Its officials say the accusers have never produced hard evidence. Now that has changed as Mandiant, an American cyber-security firm, released a detailed report on February 19th describing the activities of a curious group of hackers. Through its work protecting Western firms, Mandiant observed how these hackers broke into dozens of company networks over many years to steal vast amounts of intellectual property (IP). The bombshell is the claim, denied by the government, that this gang is actually an elite division of the People’s Liberation Army (PLA), known as Unit 61398, based in an innocuous white office building near Shanghai’s financial district (see picture). The report is worth taking seriously for several reasons. First, Mandiant has a sound pedigree: it shot to prominence by tracing the long-term hacking of the New York Times, revealed last month, back to Chinese officialdom. And, unlike previous accusers, it has meticulously documented the hackers’ methods and malware. Though the hackers (known as the “Comment Crew”) used nearly 1,000 remote servers in over a dozen countries, Mandiant traced them to networks in Shanghai near the army compound. Blame China first Not everyone is satisfied. Jeffrey Carr of Taia Global, a security consultancy, argues that this new report suffers from a “blame China first” bias, and that its methodology is not rigorous enough. Mandiant rejects this, though it accepts that the evidence points to Unit 61398’s district, rather than to its actual building. However, it is unlikely that well-organised, well-funded cybercrooks are hacking the Fortune 500 from noodle joints outside the compound. Still, it is surely right to challenge those who blame China for every ill. Apple, Facebook and Twitter have recently been breached, for example, but it appears that hackers from eastern Europe may be to blame. Iranians were probably behind a recent cyber-attack on Saudi Aramco, the world’s biggest oil firm. Robert Bigman, formerly chief information security officer for the CIA, says that Russia, Bulgaria, Romania and Ukraine deserve to join China on cybercrime’s most-wanted list. An American telecoms company recently asked Mr Carr to investigate a Chinese outfit acquired by one of its American vendors. This client wanted to be sure that its new purchase did not have ties to China’s state-sponsored cyber-hackers. It did not, but Taia discovered in the process that the Chinese company used a software-outsourcing firm that turned out to be a front for Russian intelligence.
Mandiant probably got it right, believes Dmitri Alperovitch of CrowdStrike, a security firm that got close to nailing the PLA’s hackers two years ago. Mr Bigman, the ex-CIA officer, agrees. It is unclear whether the hacking activity is orchestrated or merely tolerated by central authorities. Another reason to think this report marks a turning-point is its timing, which suggests American official blessing. Richard Bejtlich of Mandiant says the firm decided only a month ago to give away the report. Normally, private clients would pay handsomely for the detailed technical information it contains. But, mindful of the growing momentum among political leaders for action, and after discussing the report with intelligence experts, the firm released it as a way “to wage cyber war and to challenge the ‘benign China’ thesis”. The report is part of a new American “naming and shaming” effort designed to push China to rein in its hackers, reckons Bill Bishop, a Beijing-based technology expert. It might work, but he worries that if America pushes too hard the new Chinese leadership will feel boxed in. Under pressure from the PLA and public opinion, it might choose to escalate things instead. Adam Segal of the Council on Foreign Relations, an American think-tank, argues that America must be willing to use trade penalties, visa restrictions and financial sanctions to raise the cost of stealing IP. “China must see it is vulnerable,” he insists. On February 20th America announced a strengthening of its efforts to prevent the theft of trade secrets, and China was mentioned prominently. In the past many firms have been reluctant to admit they had been hacked, because of the risk of tipping off competitors and alarming investors. Perhaps Mandiant’s report will mark the moment when firms began to put collective security first. Christian Murck, head of the American Chamber of Commerce in Beijing, likens the silence to the one that surrounded counterfeiting a dozen years ago. Back then, fake goods were an enormous problem in China but Western companies did not want to speak out for fear of tarnishing their brands. In time, though, firms got together, shared information and lobbied for stronger laws and enforcement. Counterfeiting is still widespread but it is becoming a more manageable problem. Hacking might be too one day, says Mr Murck. Western victims have one further hope. Attitudes toward IP theft may be changing at the best Chinese companies. Huawei and ZTE, Chinese telecoms-equipment vendors, are at each other’s throats in a row about stolen IP. Mindray, a Chinese medical-technology pioneer, has taken former employees to court for ripping off its designs. In short, Chinese firms are starting to generate their own valuable IP and will increasingly demand that the legal system protect their assets. As they do so, they are starting to get their employees to respect IP as well. Pressure on China from abroad will remain crucial, especially because decisions in Chinese courts can still be bought or manipulated. This pressure and increased domestic awareness may start to make a difference, but change is still likely to be very slow in coming.
Smoking gun Feb 26th 2013, 13:43
Last week, PCWorld, heading all global press, released a news from its brother partnership, IDG news, detailing the question of a Security company Mandiant and China’s official response.
http://www.pcworld.com/article/2028747/new-report-says-cyberspying-group...
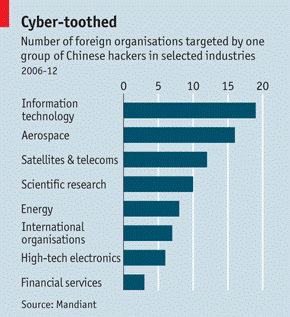
From this report’s sixth paragraph, there’s a key point of whether China’s official or military concerned interfere with the cyberattack, especially for this time. “The group has a sinister track record, according to Mandiant. Since 2006, Mandiant has observed APT1 compromise 141 companies spanning 20 major industries. Eighty-seven percent of the target companies are headquartered in countries where English is the native language, and are in industries that China has identified as strategic.” The report referred to the possible access to knowledge essential of “strategic industry” for China’s future. The aftermath of paragraph talked about the circumstance, “a variety of intellectual property, including technology blueprints, proprietary manufacturing processes, test results, business plans, pricing documents, partnership agreements, and emails and contact lists from the leadership of the victim organizations”.
Let me disclose something after some discussion with elder ones in Beijing. At the same day, the associated press chief in China’s foreign affair, Hong Lei as spokesman, refuted the saying of cyberattack directed by officials or military. Of course, some friends or bloggers who instantly read this comment may say the answer I receive from Beijing’s center is the only “in denial”. Hence, I request some relative enterprises, including Taiwan’s investors in Taiwan (small-medium size ones), but there is indeed few link with military secret. Nevertheless, I am a bit surprised of the connection between these companies and the incumbent leader Xi Jin-ping (rather than Hu and the faction of Communist Youth League, little knowing these) because Xi and these built up very close relationship from Xi’s term in Shanghai party secretary for a long time. I guess that there is some conspiracy potential of confusing Beijing’s upcoming generation in office.
Basically, an intelligence unit may make itself shed, so the dealing of communication with other fields of companies or academic should be limited as a reasonable surroundings. The number is 141, actually, of the dealing concerned but just general business. Moreover, the company, so-called unit, locates in Shanghai, rather than Beijing or major military defensive port. But there is one thing good at this case and at this moment that Xi and these companies know the key industries of English-native nation, especially for China’s development from this access. It’s so horribly good that the survey of Mandiant let me know Xi’s pros and cons on practicing policy. After all, the case affects few and the cyberattack sometimes comes from strange port of internet that officers don’t know.
By the way, in the past, Taiwan’s media know the concerned earlier than the rest of the world. This time, they have few information about this news and keep silent. It’s boring but I make complaint on this board.
Recommended 2 Report Permalink 筆者在討論區回覆這個上海的辦公室中國解放軍的「網軍部」疑雲,參考了同樣二月份,在leaders專欄和內頁內文的三篇文章
China’s cyber-hacking Getting Ugly If China wants respect abroad, it must rein in its hackers Feb 23rd 2013 |From the print edition · ·
FOREIGN governments and companies have long suspected that the Chinese hackers besieging their networks have links to the country’s armed forces. On February 19th Mandiant, an American security company, offered evidence that this is indeed so. A report, the fruit of six years of investigations, tracks individual members of one Chinese hacker group, with aliases such as Ugly Gorilla and SuperHard, to a nondescript district in residential Shanghai that is home to Unit 61398 of the People’s Liberation Army. China has condemned the Mandiant report. On February 20th America announced plans to combat the theft of trade secrets. Mandiant claims that hackers at Unit 61398 have stolen technology blueprints, negotiating strategies and manufacturing processes from more than 100, mainly American, companies in a score of industries (see article). Its report does not name the victims, but a related New York Times investigation has found evidence that hackers targeted a company providing internet security for American spooks. The hackers also gained access to the systems of an American defence contractor. Perhaps most worrying, they broke into networks of a company that helps utilities to run North American pipelines and power grids. Nobody knows how many billions of dollars cybercrime costs businesses. But pretty much everyone has come to believe that China is the most egregious offender. In this section · Getting Ugly · Bin it Related topics · Politics America is not an innocent in the world of cyber-spying. It does plenty itself, and acknowledges that these operations are a legitimate part of national security. At the same time, however, it should do more to promote the idea that everyone would gain from “cyberarms control” to set the rules of engagement. The Mandiant report shows China’s definition of national security includes outright theft. One lesson is that all companies need urgently to upgrade their defences. President Barack Obama has announced measures for greater co-operation between American firms and government agencies to share information. Many companies have been too scared to admit they have been hacked, for fear of alarming clients and investors. In their own interests, they need to open up. America also needs to make it clear to China that state-sponsored crime is unacceptable. Until now the United States has tended to complain about China’s cyberthieves behind closed doors in discussions with Chinese officials. But with more evidence emerging of China’s flagrant abuses, more naming and shaming should be considered. Control, Alt, Delete There are lessons for China’s new leader, too. Xi Jinping has come to power suggesting that China must embrace reform and show more respect for the rule of law. Now he has the chance to demonstrate that he really means this. China claims the Mandiant report is flawed and lacks “technical proof”. That is a missed opportunity. Though it goes against every instinct of the secretive Communist Party, Mr Xi could acknowledge that cybercrime emanates from state-sponsored entities and that his government will now rein them in. If he does not, China will be taken less seriously when it decries the West’s talk of a “China threat”. And Chinese companies will continue to be treated with suspicion when they seek to buy or work with businesses abroad. China should bring its army of thieves to order. From the print edition: Leaders
Chinese cyberattacks Hello Unit 61398 Feb 19th 2013, 14:51 by T.P. | BEIJING · ·
AN AMERICAN information security firm has identified a secretive Chinese military unit as the likely source of hacking attacks against more than a hundred companies around the world. In a report made public on Tuesday, the firm, Mandiant, based in Alexandria, Virginia, said it could now back up suspicions it first reported in more qualified form in 2010. The firm then said the Chinese government may have authorised the hacking activity it had traced to China, but that there was “no way to determine the extent” of official involvement. In its new report, Mandiant updates its assessment. “The details we have analysed during hundreds of investigations convince us that the groups conducting these activities are based primarily in China and that the Chinese government is aware of them,” the report said. China’s government has denied the allegations. Hong Lei, a spokesman for China’s foreign ministry, said on Tuesday that China has itself been a victim of cyber attacks, and that it enforces laws that ban such activity. “Groundless criticism is irresponsible and unprofessional, and it will not help to solve the problem," he said of the Mandiant report. According to the report, a Shanghai-based unit of the People’s Liberation Army General Staff Department, known as Unit 61398, is staffed by hundreds and possibly thousands of people specially trained in network security, digital signal processing, covert communications and English linguistics. The unit’s 12-storey building (pictured above) has been equipped with special fibre optic communications infrastructure “in the name of national defence”. Mandiant said that since 2006, it has observed attacks from this unit against at least 141 companies spanning 20 major industries, including four of the seven strategic emerging industries that China has identified in its current five-year plan. The New York Times, which hired Mandiant to investigate China-based cyber attacks against its news operations, was the first to report on the firm’s findings. Mandiant concluded that the attacks against the newspaper had come from a different Chinese source. In the case of the attacks described in the new report, Mandiant said it could not prove that the attacks came from within the military building it identified. But it concluded that this was the most plausible explanation for its findings. “Either they are coming from inside Unit 61398, or the people who run the most-controlled, most-monitored Internet networks in the world are clueless about thousands of people generating attacks from this one neighbourhood,” Kevin Mandia, the founder and chief executive of the company told the paper. Editors note: for those interested in the technological aspects of this story, theres a good discussion going on here.
Chinese cyber-attacks How to steal a trillion Feb 19th 2013, 21:49 by G.F. | SEATTLE · ·
ON FEBRUARY 19th Mandiant, a security firm, released a report alleging that hackers from a Chinese military outfit known as Unit 61398 were probably behind attacks against more than a hundred companies and government agencies around the world. Without delving into the geopolitics of the the incident, involvement in which the Chinese authorities vehemently deny (and which we write about here), Babbage decided to examine what is known about the hackers methods. In fact, Mandiants detailed account of a group it dubs APT1 (after the term Advanced Persistent Threat) will not strike internet-security wonks as particularly Earth-shattering. It reveals the use of well-known techniques coupled with publicly available software—though some proprietary software, apparently perfected over many years, was also used. What has turned heads is the duration of the attacks and the range of the groups "ecosystem" of remote-control software. This combination allowed the hackers to siphon terabytes, or trillions of bytes, of data from their victims. In many ways, the attacks resembled those criminal groups and spammers deploy against individuals and businesses. A "spearphishing" e-mail is sent, which attempts to get members of an organisation to open an attachment that appears to originate from a colleague or business partner, and contains some typical business data. Rather than a file, though, the attachment is a piece of malware. When opened, it exploits system flaws to install backdoor access to the computer. This allows remote command-and-control servers anywhere on the internet to install additional software, capture keystrokes and images on the screen, and ferret around the local network. Mandiant says the hackers sometimes used malicious remote-access toolkits readily available on the "dark side" of the internet (if not through your average Google search). But mostly they either developed or acquired at least 42 "families" of proprietary remote-access tools. Some have dates imprinted in them which indicate they were initially programmed as early as 2004, with updates added over the subsequent six years. The attacks, in other words, were carefully planned and premeditated. To fool firewalls and other software, some remote-control malware mimicked traffic patterns of legitimate internet services, like the Jabber/XMPP chat system used by Google and Facebook, among others. This allowed them to send information to and from the infected machines without raising suspicions. A lot of the insidious traffic was encrypted, but this too is commonplace for many websites and services, including Twitter and standard e-mail. APT1 tried hard to retrieve password-related information, often using common cracking tools. Before being stored a password is usually fed into an algorithm called a hash function. This converts it into an obscure string of symbols, or a "hash", that offers no clue as to the original input. The function is irreversible, so you cannot work back from a hash to the password. You can, however, run different words through a hash function and compare the resulting hash with the one stored. Many such "brute-force" attacks use large dictionaries of common and less common passwords. As a number of companies discovered last year, poor passwords make for easy pickings. Some clever tools actually let an attacker log into a system using the encrypted form of a password, dispensing with the need to crack it. There is also evidence of hackers gleaning network information in order to make connections within a network and infect more machines. Some of the backdoors captured credentials for virtual private networks (VPNs), which allow direct remote access to a network without having to rely on a single compromised computer. Once in, the eavesdroppers used e-mail-extraction tools, which Mandiant says are unique to the group, to pull messages or attachments of interest from a users inbox, both current and archived. Many of these exploits remain in place, sometimes in multiple forms in case one is found and removed. Hackers stuffed any files deemed of interest into compressed archive formats and added password protection before whisking them away. For all their sophistication, however, the hackers could display incredible insouciance. For example, APT1 registered domain names for some of its systems and used either a Shanghai mailing address or included an e-mail address tracked via a simple Google search to a Shanghai-based organisation. Remote-access sessions using a Microsoft tool nearly always originated from hacker machines using the simplified Chinese keyboard layout. Backdoor software included "path" information, revealing details about folder organisation on programmers computers, as well as the date software was written. Most absurdly, perhaps, some hackers used the remote sessions on compromised machines to access their personal Facebook, Twitter or Gmail accounts. Among others, Mandiant has fingered a certain Wang Dong, who uses the handle Ugly Gorilla and who registered one of the command-and-control domains. It also included a screen shot of a Gmail inbox of another hacker. Mandiant is bracing for reprisals.
附上筆者在回文中引用的PCWorld的文章原文:(https://www.pcworld.com/article/2028747/new-report-says-cyberspying-group-linked-to-chinas-army.html)
New report says cyberspying group linked to Chinas armyA new report traces a large cybersecurity threat group to China’s People’s Liberation Army, specifically an unit that goes under the cover name “Unit 61398”. Security company Mandiant said in a report released Tuesday that an Advanced Persistent Threat group it called APT1 was one of the most persistent of China’s cyberthreat actors because of its likely government support. “In seeking to identify the organization behind this activity, our research found that People’s Liberation Army (PLA’s) Unit 61398 is similar to APT1 in its mission, capabilities, and resources,” Mandiant said in its report. “PLA Unit 61398 is also located in precisely the same area from which APT1 activity appears to originate.” Unit 61398 is said to be located in a 130,663 square-foot building on Datong Road in Gaoqiaozhen, in the Pudong New Area of Shanghai. The nature of the work of “Unit 61398” is considered by China to be a state secret, but Mandiant said it believes it engages in harmful computer network operations. The group has a sinister track record, according to Mandiant; since 2006, it has observed APT1 compromise 141 companies spanning 20 major industries. Eighty-seven percent of the target companies are headquartered in countries where English is the native language, and are in industries that China has identified as strategic. APT1 uses tools that the security firm finds have not been used by other groups, including two tools for stealing emails called GETMAIL and MAPIGET. Once the group has established access, it periodically revisits the victim’s network over several months or years to steal a variety of intellectual property, including technology blueprints, proprietary manufacturing processes, test results, business plans, pricing documents, partnership agreements, and emails and contact lists from the leadership of the victim organizations, Mandiant said. China’s Foreign Ministry said on Tuesday the nation is firmly opposed to hacking, and has supported regulation to prevent cyberattacks. The government has previously denied accusations that Chinese hackers attacked major newspapers. The country has also been the victim of hacking, with the number one origins for those attacks coming from the U.S., said ministry spokesman Hong Lei during a press conference. “Cyber attacks are transnational and anonymous. Its very hard to trace the origins of the attacks. I don’t know how this evidence in the relevant report is tenable,” he added. With additional reporting from Michael Kan of IDG News Service in Beijing Note: When you purchase something after clicking links in our articles, we may earn a small commission. Read our affiliate link policy for more details.
|
|
| ( 心情隨筆|心情日記 ) |